Spoofed Email Chain Phishing Attacks Are on the Rise—Is Your Business Ready?
Published: October 14, 2024
Spoofed email chain phishing attacks are fast becoming one of the most dangerous cyber threats facing businesses today. What makes these attacks particularly alarming? Cybercriminals don’t need to hack into your system—they simply mimic an ongoing email conversation. These attackers forge email threads, making it look like a legitimate conversation between your company’s executives and external business partners, tricking employees into providing sensitive information or authorizing fraudulent payments.
It’s a sophisticated, sneaky attack that can cause major financial and data losses without ever compromising your network. Let’s dive into how spoofed email chain attacks work, why they’re so dangerous, and how you can protect your business.
Short on Time? Listen Instead!
What Are Spoofed Email Chain Phishing Attacks?
A spoofed email chain phishing attack occurs when a cybercriminal forges an email that looks like it’s part of an ongoing conversation. The attacker doesn’t actually have to study past email threads or infiltrate your email system. Instead, they predict what might seem like a legitimate, ongoing discussion—often between a high-ranking executive and an external business partner.
By inserting themselves into what looks like a real thread, they request sensitive information or urgent payments. Because the email looks like it’s part of an important conversation, employees may act without thinking twice.
For example, an attacker might pretend to be your CFO and request immediate payment to a new vendor, providing fake banking details. The message is carefully crafted to sound like a continuation of a real conversation between your company and an external party, making it highly convincing.
Why These Attacks Are So Dangerous
Now that we’ve established the importance of a DRP, let’s dive into how to build one that’s strong enough to withstand any IT disaster. Here are some key strategies:
No System Breach Required
Unlike traditional phishing attacks that involve infiltrating your email system, spoofed email chain attacks rely on deception rather than hacking. Attackers can create these fraudulent email threads without needing access to your internal communications.
Looks Legitimate
Because these attacks mimic real email conversations—complete with familiar names, email signatures, and business language—employees are less likely to question their authenticity. The attackers are masters at crafting messages that seem normal, urgent, and important.
Targets Any Employee
Spoofed email chain attacks don’t only target high-level executives. Any employee involved in financial transactions or sensitive business operations can be tricked into making a payment or sharing private information.
Creates Urgency
Attackers often frame their requests as urgent, forcing employees to act quickly without verifying details. A fraudulent email may claim there’s a time-sensitive issue that needs to be addressed immediately—leaving little time for second-guessing.
Real-Life Examples of Spoofed Email Chain Attacks
Example: Fake Invoice Request from an Ongoing Email Thread
Scenario: You’re part of the accounting team at a mid-sized company. One day, you receive an email that seems to be part of an ongoing thread discussing payment for advisory services. The email, appearing to come from a trusted external vendor, requests immediate payment of an overdue invoice.
Spoofed Email Chain:
- From: A malicious sender posing as a trusted vendor ([SPOOFED] <EMAIL@MALICIOUS_DOMAIN>)
- To: Accounting <Accounting@[TARGET_DOMAIN]>
- Subject: “Past Due Advisory Bill Attached – Consultation Platform”
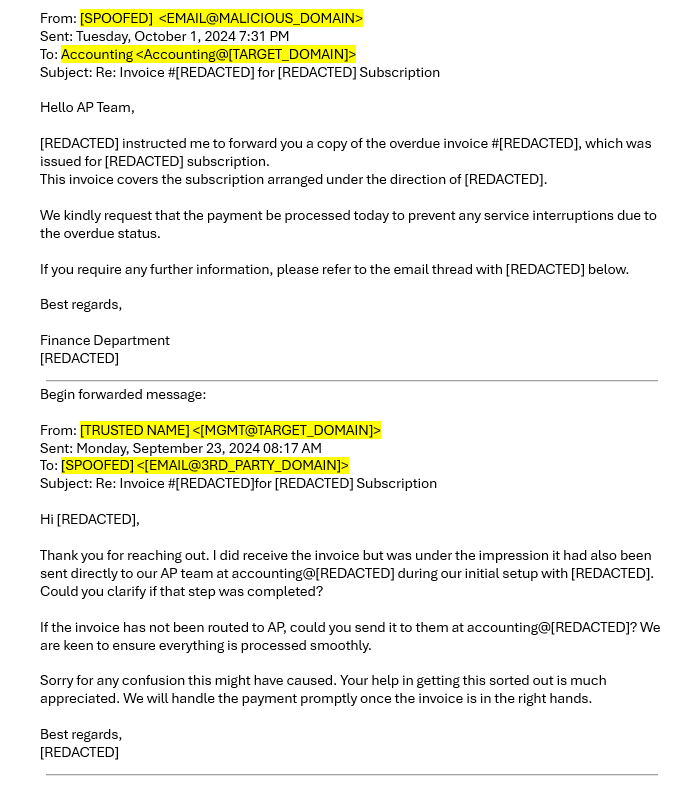
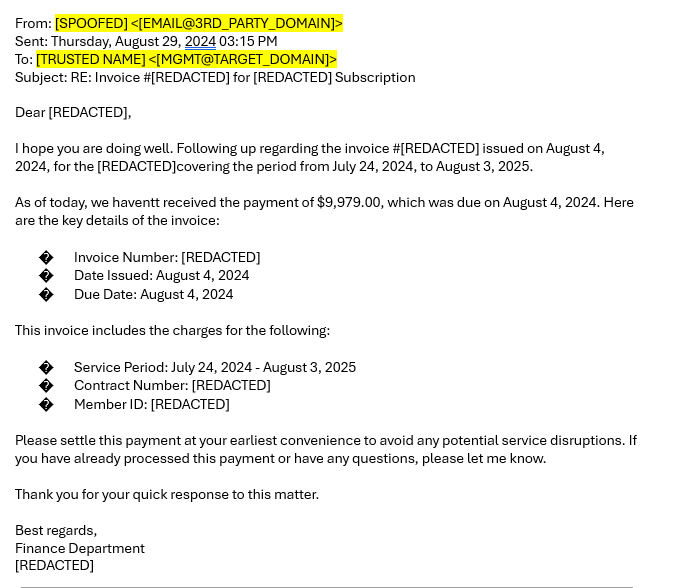
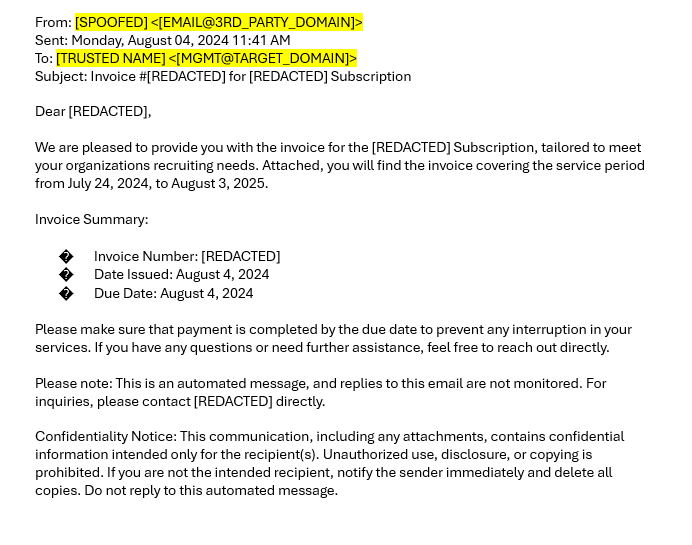
The email thread shows that a trusted figure in your organization could be your CFO (MGMT@TARGET_DOMAIN) had previously confirmed the accuracy of the invoice, making it seem legitimate. The request for payment seems urgent, and the attached invoice looks real, complete with a breakdown of services and payment details.
What Really Happened: The attacker forged the entire email thread to make it look like a genuine conversation between your CFO and the external vendor. In reality, the vendor’s email was spoofed, and the payment request was fraudulent. The urgency and tone of the email pressured the accounting team into processing the payment without verifying it through proper channels.
How to Protect Your Business from Spoofed Email Chain Phishing Attacks
Though these attacks are sophisticated, there are steps you can take to minimize your risk:
1. Verify All Financial Requests
Establish a verification process for financial requests. Require verbal or secondary confirmation (such as a phone call) before authorizing any payments, especially if the request involves new banking information or an unusual amount. A quick verification could save your company from transferring money to fraudsters.
2. Enable Multi-Factor Authentication (MFA)
Even though spoofed email chain attacks don’t require a system breach, MFA can help protect against other types of phishing that might lead to unauthorized access. MFA ensures that even if a password is compromised, another layer of security is in place.
3. Educate Employees About Phishing Tactics
Regular training is crucial. Ensure your employees understand the risks of spoofed email chains and know how to scrutinize even seemingly legitimate emails, especially when they involve sensitive information or financial transactions.
4. Examine Links and Attachments Carefully
Teach employees to hover over links before clicking and to be cautious with attachments—even if the email appears to come from a trusted source.
5. Use Advanced Email Security Tools
Invest in email security solutions that can detect unusual email patterns, spoofed domains, or changes in email headers. These tools can help block phishing attempts before they reach your employees’ inboxes.
6. Monitor VIP Communications
Executives and senior managers are often the primary targets of these attacks. Set up additional security measures for their email accounts, and closely monitor any unexpected communication involving them.
What to Do If You've Fallen for a Spoofed Email Chain Attack
If you suspect you’ve received a spoofed email, act immediately:
1. Report the Incident
If sensitive information has been compromised, notify your business partners or vendors whose names may have been used in the spoofed email, and report the incident to cybersecurity authorities.
2. Stop Any Financial Transactions
If the email involved a payment request, freeze any transfers until the request can be confirmed through another communication channel, such as a phone call or an in-person conversation.
3. Warn Your Colleagues
Alert your team to the suspicious email. If one person has been targeted, others may be next.
Spoofed email chain phishing attacks are dangerous because they exploit trust and familiarity. These attacks don’t rely on hacking your systems but on manipulating employees into acting on fake emails that seem legitimate. The key to protecting your business lies in raising awareness, verifying suspicious requests, and implementing strong security practices.
Stay alert, and don’t let your business fall victim to these sophisticated scams. For more information on how to protect your business from phishing attacks and other cyber threats, contact Accent Consulting for expert advice and tailored solutions.
Reach Out To Cyber Secure Your Business
Recent Posts
-
 3 Reasons Why SMBs Can’t Afford to Ignore AIMay 21, 2025/0 Comments
3 Reasons Why SMBs Can’t Afford to Ignore AIMay 21, 2025/0 Comments -

-

-
 DeepSeek: Unlocking the Future of Business Decision-MakingJanuary 30, 2025/
DeepSeek: Unlocking the Future of Business Decision-MakingJanuary 30, 2025/ -
 How Local IT Support Powers Ag Business Success in IndianaJanuary 16, 2025/
How Local IT Support Powers Ag Business Success in IndianaJanuary 16, 2025/ -
 Transform Your Business in 2025: 5 Must-Have Tech ResolutionsJanuary 6, 2025/
Transform Your Business in 2025: 5 Must-Have Tech ResolutionsJanuary 6, 2025/ -
 Accent Consulting’s Annual Holiday Party 2024December 11, 2024/
Accent Consulting’s Annual Holiday Party 2024December 11, 2024/


